If you use the command-line interface (CLI) to manage the switch from a remote system, you can use Secure Shell (SSH) to establish a secure connection. SSH uses public-key cryptography to authenticate the remote computer.
Use the Secure Shell Configuration page to configure the settings for secure command-line based communication between the management station and the switch. To display the Secure Shell Configuration page, click Security > Secure Shell > Configuration in the navigation menu.
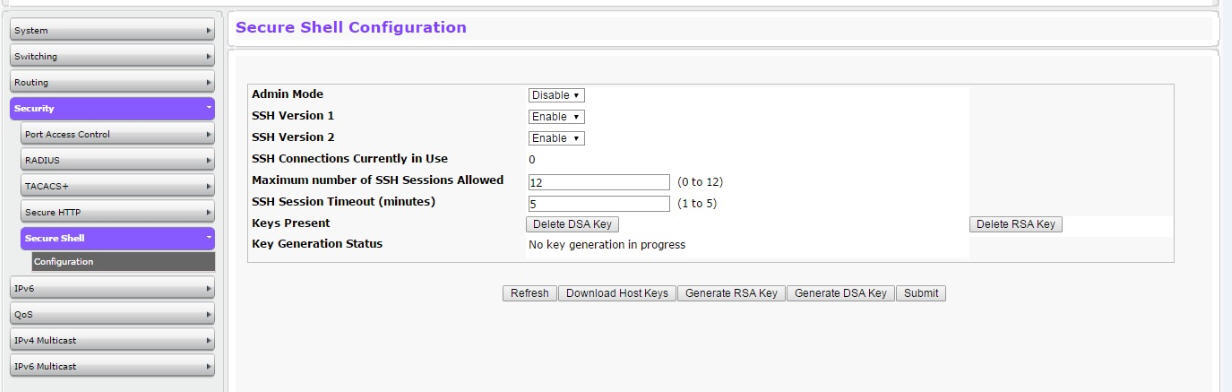
Secure Shell Configuration Fields
Field |
Description |
|---|---|
Admin Mode |
This select field is used to Enable or Disable the administrative mode of SSH. The currently configured value is shown when the web page is displayed. Setting this value to disable shuts down the SSH port. If the admin mode is set to disable, then all existing SSH connections remain connected until timed-out or logged out, but new SSH connections cannot be established. The default value is Disable. |
SSH Version 1 |
This select field is used to Enable or Disable Protocol Level 1 for SSH. The currently configured value is shown when the web page is displayed. The default value is Enable. |
SSH Version 2 |
This select field is used to Enable or Disable Protocol Level 2 for SSH. The currently configured value is shown when the web page is displayed. The default value is Enable. |
SSH Connections in Use |
Displays the number of SSH connections currently in use in the system. |
Maximum Number of SSH Sessions Allowed |
This select field is used to configure the maximum number of inbound SSH sessions allowed on the switch. The currently configured value is shown when the web page is displayed. The range of acceptable values for this field is (0-12). |
SSH Session Timeout (Minutes) |
This text field is used to configure the inactivity timeout value for incoming SSH sessions to the switch. The acceptable range for this value is (1-160) minutes. |
Key Present |
Displays True if Secure Shell (ssh) keys present /False if the Secure Shell (SSH) keys not present. |
Key Generation Status |
Displays the generation status of the Secure Shell (SSH) keys.
|
For the switch to accept SSH connections from a management station, the switch needs SSH host keys or certificates. The switch can generate its own keys or certificates, or you can generate these externally and download them to the switch.
To download an SSH host key from a TFTP server to the switch, use the instructions in “Downloading SSL Certificates”. However, from the File Type field on the File Download page, select one of the following key file types to download: