The following set of options can be managed in security settings:
To access security settings preview pane, click Security > Security Settings. The Security Settings page is displayed.
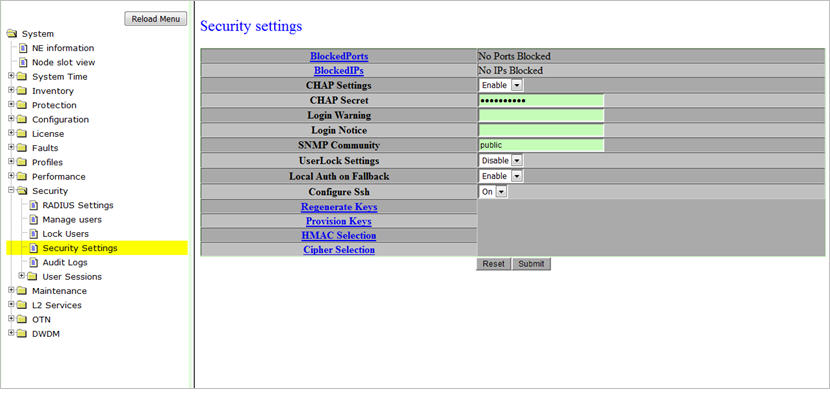
Security settings parameters
Parameter |
Description |
|---|---|
BlockedPorts |
Clicking on this link displays the list of ports Blocked. |
BlockedIPs |
Clicking on this link displays the list of IPs Blocked. |
CHAP Settings |
Allows you to select the value from the drop-down list. |
CHAP Secret |
Allows you to edit/enter the CHAP secret. |
Login Warning |
Allows you to enter the warning that is displayed in the Login page. |
Login Notice |
Allows you to enter the notice that is displayed in the Login page. |
SNMP Community |
Allows you to enter the community name to which this entry grants access. A community name is a name associated with the switch and with a set of SNMP managers that manage it with a specified privileged level. The length of name can be up to 16 case-sensitive characters. |
UserLock Settings |
Allows you to enable and disable UserLock Settings. |
Local Auth on Fallback |
Allows you to define the settings for fall back.
|
Configure Ssh |
Allows you to turn on Secure Shell (Ssh) protocol. The protocol secures the sessions using standard cryptographic mechanisms. |
Regenerate Keys |
Allows you to regenerate keys. Clicking on this link allows you to select the key type for Secure Shell (Ssh) from the following:
|
Provision Keys |
Clicking on this link allows you to provision Secure Shell (ssh) keys. You can enter the location of the public and private key files, and select the key type. |
HMAC Selection |
Clicking on this link allows you to select the Hmac to be supported. HMAC is used for calculating message authentication code involving a cryptographic hash function(MD5 and SHA1) in combination with a secret key. HMAC can verify the data integrity and authenticity of a message. The size of the output for Hmacs are as follows.
|
Cipher Selection |
Clicking on this link allows you to select the Cipher to be supported. In Ciphers, “aes” and “des” are symmetric-key encryption standards, and the number following specifies the key size. |