This section describes the MAC-based VLAN configuration and summary.
If a packet is untagged or priority tagged, the device shall associate it with the VLAN which corresponds to the source MAC address in its MAC-based VLAN tables. If there is no matching entry in the table, the packet is subject to normal VLAN classification rules of the device. Use the MAC-based VLAN Configuration page to map a MAC entry to the VLAN table. After the source MAC address and the VLAN ID are specified, the MAC-to-VLAN configurations are shared across all ports of the switch.
To display the MAC-based VLAN Configuration page, click Switching > MAC-based VLAN > Configuration in the navigation menu.
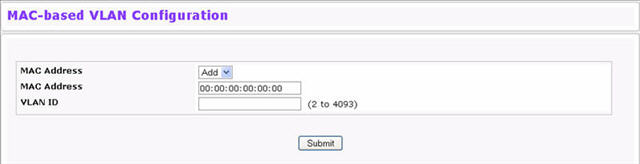
MAC-based VLAN Configuration Fields
Field |
Description |
|---|---|
MAC Address |
Specifies the source MAC address to map to a VLAN. |
VLAN ID |
Specifies the VLAN to which the source MAC address is to be bound. |
If you make any changes, click Submit to apply the changes to the system.
Use the MAC-based VLAN Summary page to view information about the MAC-to-VLAN mappings configured on your system.
To display the MAC-based VLAN Summary page, click Switching > MAC-based VLAN > Summary in the navigation menu.
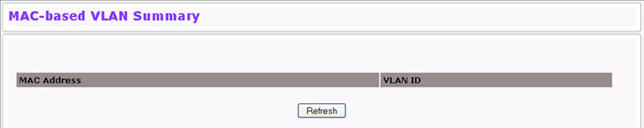
MAC-based VLAN Summary Fields
Field |
Description |
|---|---|
MAC Address |
Specifies the source MAC address to map to a VLAN. |
VLAN ID |
Specifies the VLAN to which the source MAC address is to be bound. |
Click Refresh to reload the page and display the most current information.